As you know, we installed and configured our pfSense system in the previous post, but I could not show how we add rules because of length of the post. In this post, we’ll see how we add rules to block or pass special requests. As I said before, I’m not a specialist so I can show just basic scenarios such as blocking ping requests, remote desktop requests. Also, I can say that I have these experiences thanks to my some tasks/homework etc. Anyway, they are like fundamental so after understand them, we can create our rules for our needs.
Before we begin, it will be so good to explain the environment. We have two subnets, a computer in each subnets and firewall to route and block/pass 🙂
Subnets and Computers
- 10.0.5.x – 10.0.5.21 (PC) / (Gateway: 10.0.5.10) -> A device
- 10.0.6.x – 10.0.6.21 (PC) / (Gateway: 10.0.6.10) -> B device
We set firewall interface IP addresses as these gateway addresses in the previous post, you can check. So, requests which are to out of the LAN have to redirect to firewall device.
Example Scenario 1: Ping (10.0.5.21 > 10.0.6.21)
In our first example, A device can send ping packets to B device while B can’t to A.
The packet which comes from to the firewall’s interface is coming from A device, so we can add this rule in the interface which was assigned for the subnet of A device. We assigned OPT1 interface for 10.0.5.x subnet so we’ll add this rule in this interface.
Firewall -> Rules -> OPT1 -> Add
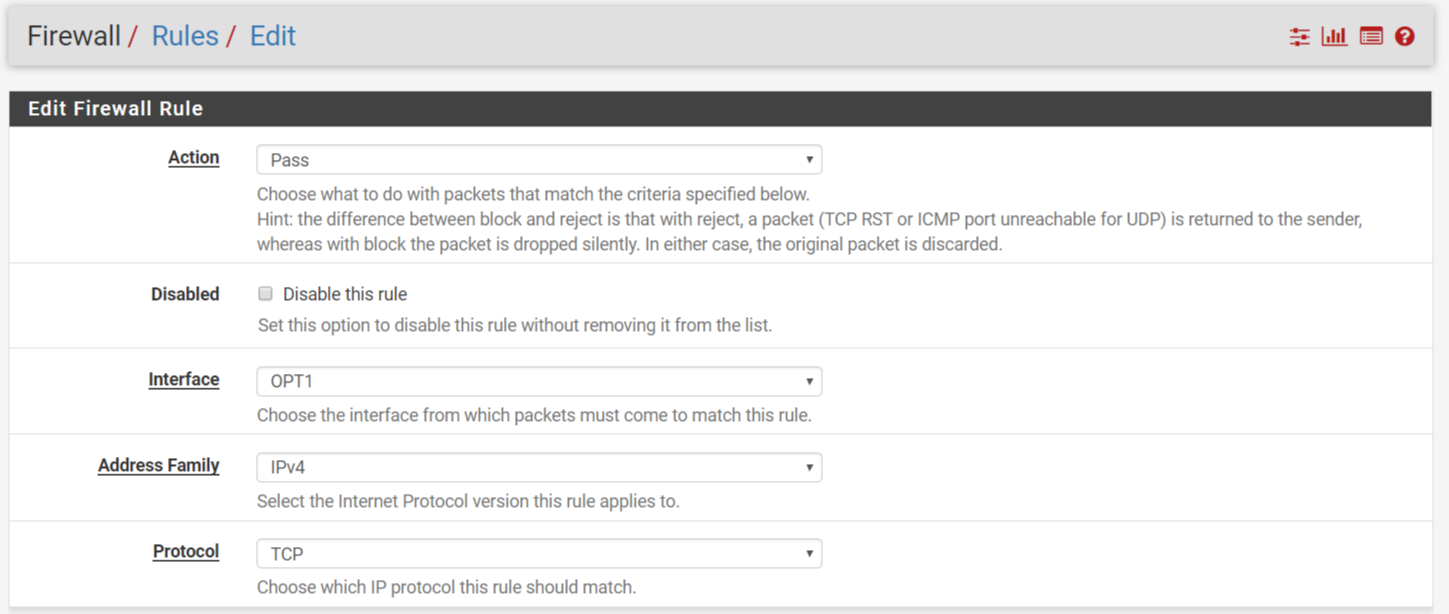
Here is the page after we click “Add” button.
Now, we’ll set protocols, port numbers, interfaces, devices etc. We will let ping packets to pass if they have direction from A to B, so our protocol will be ICMP because of ping service.
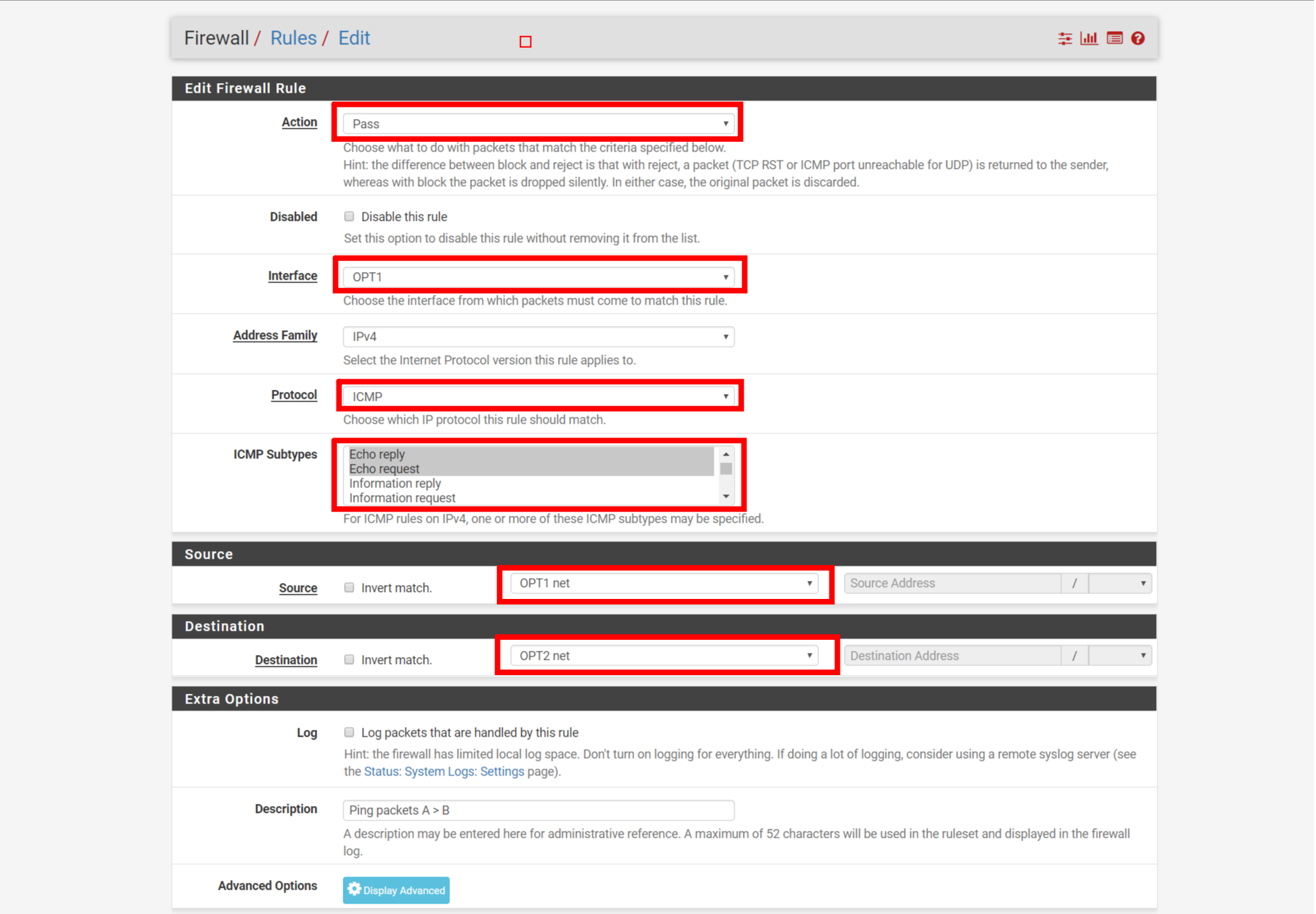
Configuration for OPT1
Firewall -> Rules -> OPT2 -> Add
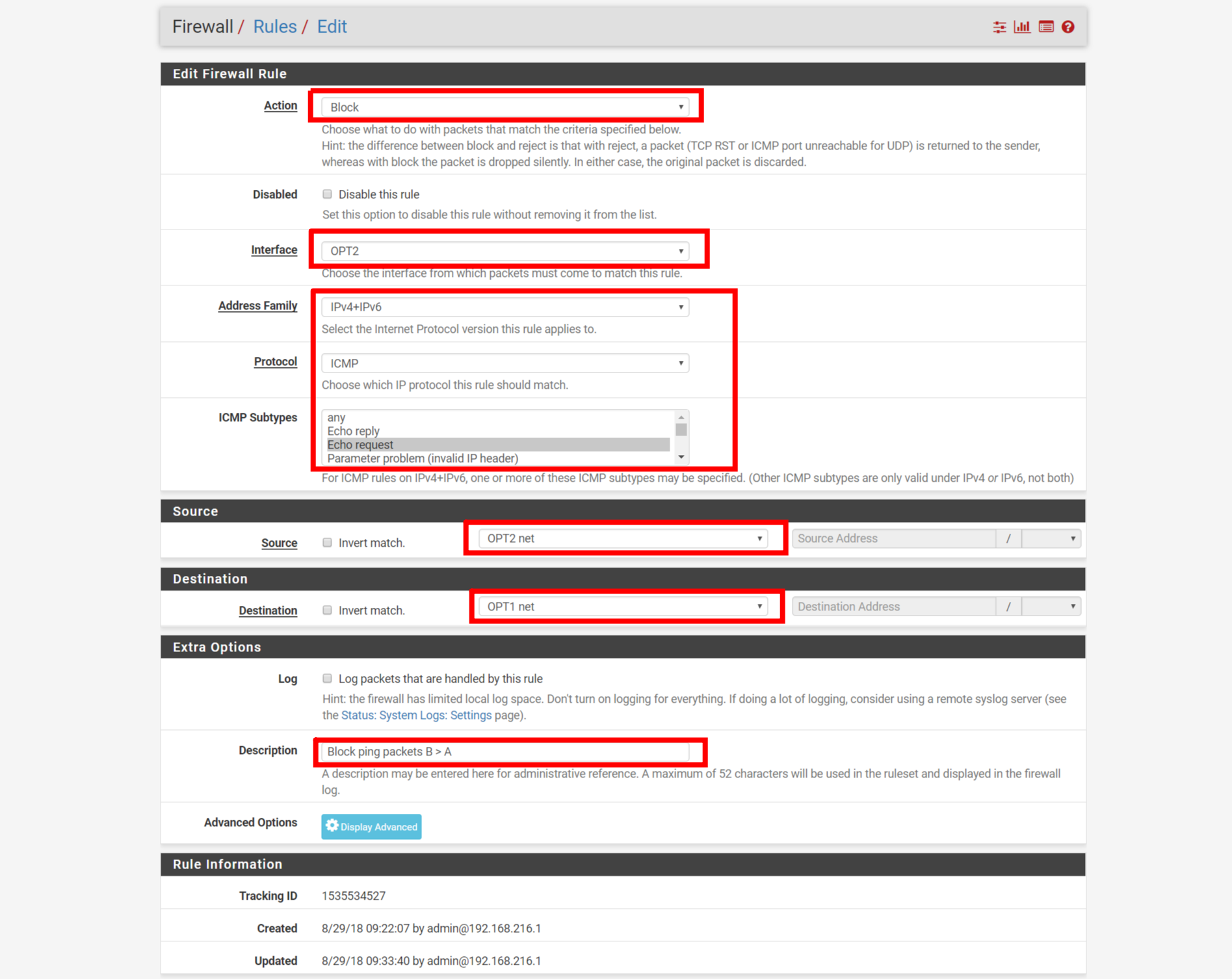
Configuration for OPT2, we can use IPV4 + IPV6 by our needs.
After apply the rules, it may be taken a few secs/mins to affect.
Here are the results:
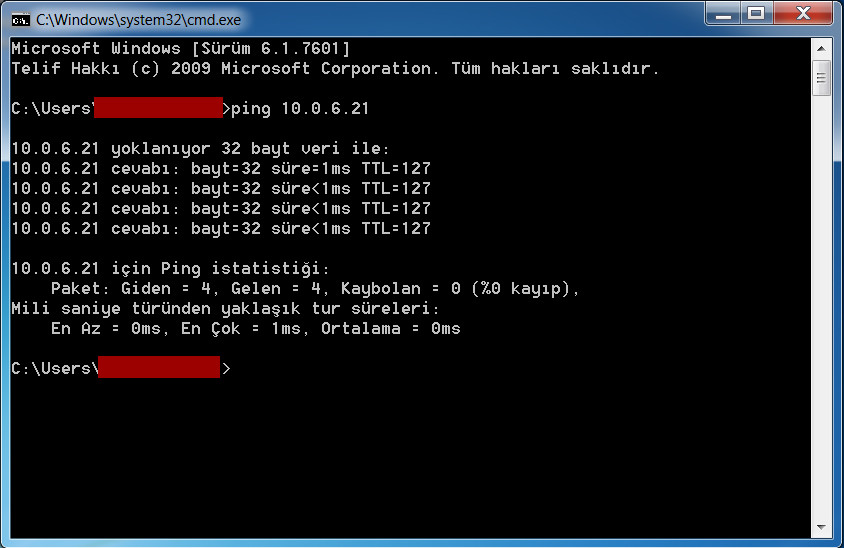
A > B allow
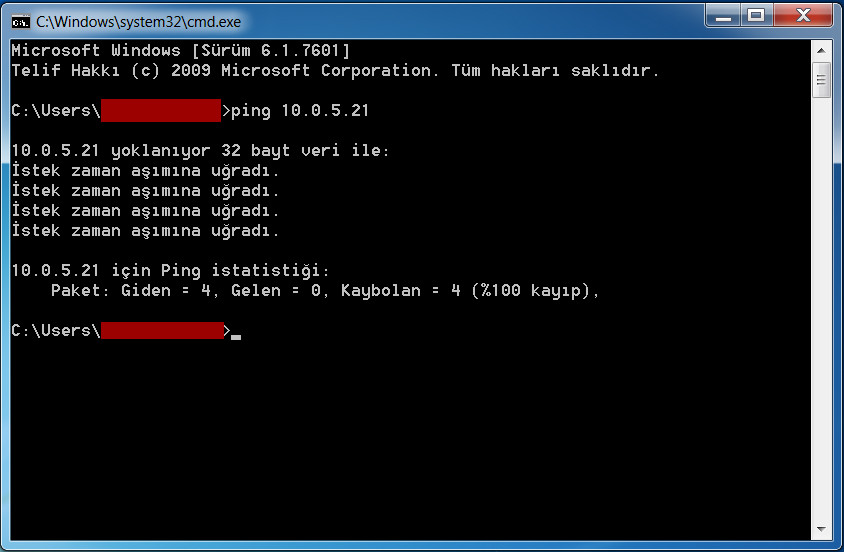
B > A block
In the next post, I’ll write about blocking or allowing RDP connection.



Leave a Reply